offensive security vs defensive security In today’s ever-evolving cybersecurity landscape, two fundamental approaches dominate the field: offensive security and defensive security. Each of these offensive and defensive strategies plays critical and major roles in protecting important digital assets in our current reality, but they differ significantly and pivotally in their goals and methodologies that are based on them to achieve their basic purposes. This article delves into the realms of offensive and defensive security, exploring their definitions, their differences, and the debate over which approach is best. In addition, we will give you insights on where you can learn offensive and defensive security skills to stay ahead in cybersecurity.
What is Offensive Security?
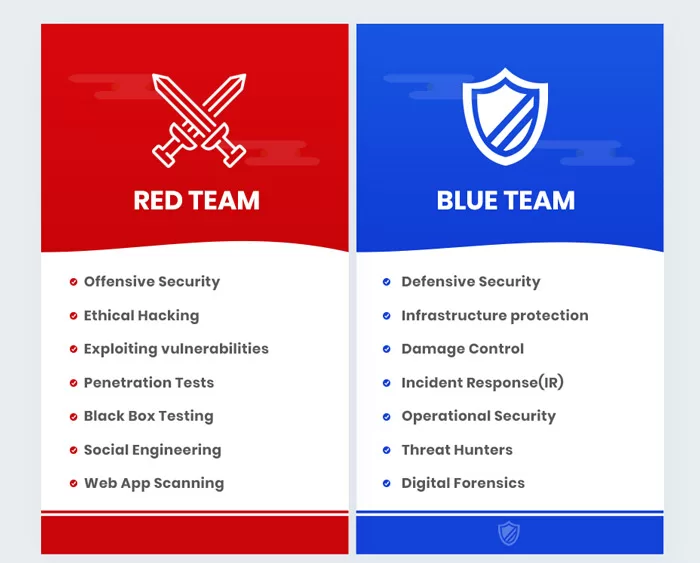
Offensive security is known by more than the name “backdoor hacking” or “red team”, and it is based on identifying vulnerabilities in systems, networks or applications effectively and ethically so that administrators can control them and prevent any room for unethical things. It also includes creating systems that simulate cyber attacks in the real world to assess the security situation of the organization and identify potential vulnerabilities in order to work on finding solutions to deal with them, which protects us in the future from exposure to information attacks. Offensive security professionals, known as ethical hackers or penetration testers, use their skills to exploit vulnerabilities, gain unauthorized access, and test the effectiveness of an organization’s defensive measures.
The primary goal of offensive security is to identify vulnerabilities and address them proactively and turn them into strengths before competitors use them and destroy the network system in the organization. By embracing the attacker mindset, offensive security professionals help organizations strengthen their defenses, enhance incident response capabilities, and reduce the risk of successful cyberattacks. As standing and waiting for a problem to occur in the system until we start to solve it is no longer a way of thinking commensurate with our current fast era
clslearn offers you the best courses in the course of Offensive Cyber Security And CTF
What is Defensive Security?

Defensive security, also known as the “blue team”, relies on establishing measures to protect systems, networks and data from potential cyber threats that are not discovered by chance or by surprise. Defense security specialists work on building, developing and maintaining strong security structures, policies and procedures that act as a wall standing in front of those who want to break into the systems of companies and institutions in order to obtain information. They continuously monitor networks, detect and respond to security incidents, and implement countermeasures to mitigate risks. Before the risks exist, they discover them through large and continuous experiments that they do on the networks
Defensive security works to create a secure environment by using a combination of preventive and responsive measures such as firewalls, intrusion detection systems, encryption, access controls, security awareness training and more emerging strategies over time. In order to build many layers that play the role of protection from external and internal threats, in addition to reducing the impact of successful attacks and ensuring business continuity.
What are the differences between Offensive and Defensive Security?
Goals:
Offensive security focuses on improving the protection system in general by testing and identifying vulnerabilities in order to solve them and discover them early so that there is no surprise. Defensive security aims to actually protect systems from potential attacks and minimize risks.
Approach:
Offensive security uses the mentality of the attacker, and tries to exploit weaknesses and turn them into strengths through which he can find an unauthorized way to enter systems. Defensive Security takes a proactive approach, no surprises here, and focuses on proactive prevention, detection, and response to potential threats.
Skills:
Offensive security professionals need an in-depth knowledge of hacking techniques, how to use them, develop them, and find solutions for them to protect their systems in the future. Defense security professionals need expertise in areas such as network security, incident response, security engineering, and risk management. Dealing with risks before they happen
methodologies:
Offensive security involves increased diligence in penetration testing, assessment of vulnerabilities, and social engineering to identify and quantify them. Defensive security implements measures such as firewalls, building layers of walls, intrusion detection systems, and encryption to protect systems and data.
Get to know about : 10 TOP OFFENSIVE SECURITY TOOLS
Offensive Security VS Defensive Security – Which is better?
Is offensive security or defensive security better? In order to get an objective answer, it depends on a set of criteria, which are: The specific needs and priorities of the organization. Both approaches are critical to maintaining a strong security posture.
Offensive security is a proactive view of problems and vulnerabilities, and initially generates valuable insights into potential vulnerabilities, vulnerabilities, and attack vectors in an organization. It helps identify gaps in security controls and reinforces defensive measures. By adopting offensive security practices, organizations can proactively identify vulnerabilities and remediate them before malicious actors can exploit them.
On the other hand, defensive security focuses on building resilient security structures, implementing preventive measures, and responding effectively to incidents. It aims to reduce the likelihood and impact of successful attacks, ensure business continuity and protect valuable assets.
In summary, a balanced approach that combines offensive and defensive security is the ideal strategy for companies to follow. While offensive security helps detect vulnerabilities, defensive security ensures the implementation of appropriate defenses to protect against potential threats, which makes each strategy individually incomplete and in need of the other. Organizations must adopt a comprehensive cybersecurity strategy that includes offensive and defensive measures to ensure high protection of their networks
Get to know about ENHANCING CYBERSECURITY WITH SOC AS A SERVICE (SOCAAS)
Where to learn Offensive Security and Defensive Security?
Several reputable training programs and resources are available for learning offensive and defensive security skills:
Offensive security:
- The Offensive Security Certified Professional (OSCP) certification provides hands-on penetration testing training so that the trainee can learn about different penetration strategies that could have happened to your corporate security networks.
- The Certified Ethical Hacker (CEH) program provides knowledge and skills in ethical hacking and penetration testing so that you can build layers of networks to withstand various hacker attacks.
- Bug bounty platforms such as HackerOne and Bugcrowd allow individuals a range of attack strategies that will help them learn the hacker’s ways to infiltrate networks.
Defensive security:
- The Certified Information Systems Security Professional (CISSP) focuses on information management, methods and strategies for protecting and preserving it from attacks and vulnerabilities.
- The Certified Information Security Manager (CISM) provides expertise in managing, designing, and evaluating enterprise security programs.
- SANS offers several courses and certifications, such as the GIAC Certified Incident Handler (GCIH) and Certified Intrusion Analyst (GCIA).

In the field of cybersecurity, both offensive and defensive security play vital roles in protecting digital assets as each one plays a complementary role to the other. Offensive security helps identify weak points so that no future surprise occurs that will have an impact on companies and their security system, while defensive security implements procedures to prevent, detect, respond to potential threats, deal with them with methods and strategies, and build layers of networks capable of confronting cyber attacks.
The choice between offensive security vs defensive security depends on determining the organization’s needs, its resources, and its future goals. Often the balanced approach that combines the two strategies is the most effective because it is able to face all the problems and attacks that are likely to attack information networks. To learn offensive security skills, certifications such as OSCP and CEH, as well as bug bounty platforms, provide hands-on training. For defense security, certifications such as CISSP and CISM, along with training programs from institutions such as the SANS Institute, provide comprehensive knowledge and skills. Because of the technological advancement in our modern era, it is necessary to continue working and knowing all the developments in the field of cybersecurity so that you can keep up with everything new.