- Courses
 Business Management
Business Management IT Networks and ITSM
IT Networks and ITSM Data Management
Data Management Software Development
Software Development Digital Transformation
Digital Transformation Graphic Design
Graphic Design
- Learning Paths
- Vendors






Get your team certified and ready to tackle the challenges of the ever-changing privacy landscape.
CISA Certification instantly declares your team’s expertise in building and implementing privacy solutions aligned with organizational needs and goals.
CISA proves your team has the technical skills and knowledge it takes to assess, build and implement a comprehensive privacy solution while enhancing business value, customer insights and trust—ultimately improving your organization’s image.
In a World Full of Auditors, be a CISA
Domain 1—INFORMATION SYSTEMS AUDITING PROCESS
Providing audit services in accordance with standards to assist organizations in protecting and controlling information systems. Domain 1 affirms your credibility to offer conclusions on the state of an organization’s IS/IT security, risk and control solutions.
Planning
Execution
Domain 2—Governance and Management of IT
Domain 2 confirms to stakeholders your abilities to identify critical issues and recommend enterprise-specific practices to support and safeguard the governance of information and related technologies.
IT Governance
IT Management
Domain 3—Information Systems Acquisition, Development and Implementation
Information Systems Acquisition and Development
Information Systems Implementation
Domain 4—INFORMATION SYSTEMS OPERATIONS AND BUSINESS RESILIENCE
Domains 3 and 4 offer proof not only of your competency in IT controls, but also your understanding of how IT relates to business.
Information Systems Operations
Business Resilience
Domain 5—Protection of Information Assets
Cybersecurity now touches virtually every information systems role, and understanding its principles, best practices and pitfalls is a major focus within Domain 5.
Information Asset Security and Control
Security Event Management
The course is suited specifically for all experienced individuals working in Information security areas which may include:





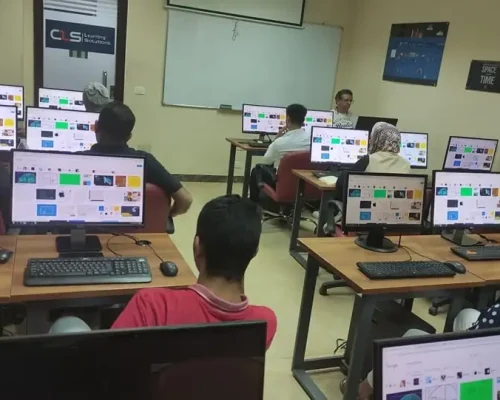





We have been in the market since 1995, and we kept accumulating experience in the training business, and providing training for more than 200,000 trainees ever since, in Egypt, and the MENA region.
CLS facilities are well-equipped with strong hardware and software technologies that aid both students and trainers lead very effective smooth training programs.
We provide our clients with the best solutions, customized to their specific needs and goals. Our team is highly qualified to answer whatever questions you have.
CLS is an authorized and accredited partner by technology leaders. This means that our training programs are of the highest quality source materials.
We keep tabs on every change in the market and the technology field, so our training programs will always be updated up to the World-class latest standards, and adapted to the global shape-shifting job market.
We select the best instructors, who are certified from trustworthy international vendors. They share their professional experience with the Trainees, so they can have a clear hands-on experience.



































I`m attending now CEH Training with Eng Mohamed Hamdy ,CISSP Training with Eng Mohamed Gohar, I really learned a lot from him , everything here in CLS is very satisfying including facilities .
We took a series of courses as the digital Transformation Unit of the ministry . we just finished CRISC Certification Training with DR Adel Abdel Meneim . Thank you CLS for all your efforts, we really appreciate it
Me and my colleagues are working in a government Organization, We took a no. of cyber security trainings with CLS starting with CEH and CISSP. we liked every thing the instructors, the stuff and whole environment
I`m attending ASP.NET Core with MVC Training with Eng Mohamed Hesham , I really learned a lot from him , everything here in CLS is very satisfying including facilities .Thanks you all team.
Qualifying the cadres of digital transformation units in government agencies moving to the administrative capital .Thanks CLS
I`m attending ASP.NET Core with MVC Training with Eng Mohamed Hesham , I really learned a lot from him , everything here in CLS is very satisfying including facilities .Thanks you all team.
I`m attending now CRISC Training with DR Adel Abdel Meneim , I really learned a lot from him , everything here in CLS is very satisfying including facilities , locations and the team.
I`m attending ASP.NET Core with MVC Training with Eng Mohamed Hesham , I really learned a lot from him , everything here in CLS is very satisfying including facilities .Thanks you all team.

Seize the moment, Learn with CLS, The Top-Rated Training Provider in Egypt since 1995, 28 Years of Experience Training Businesses and People in Egypt and Mena region.
© 2024 - CLS Learning - Solutions | All Rights Reserved.